The contexts and their logical status must be correctly defined. Inaccuracies in the logic can have an undesirable impact on the user.
To analyze what exactly led to the undesired action, it is necessary to check the status of the respective context for its correctness.
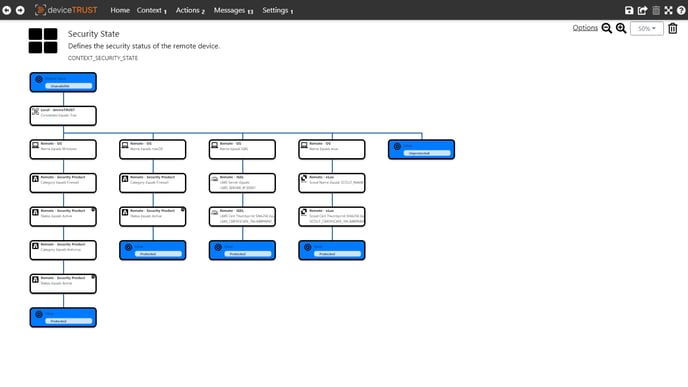
In the following example, the context SECURITY STATE was defined, which indicates the security state of the remote device the user uses to access the virtual session. Based on the logical configuration of the context SECURITY STATE, the values UNAVAILABLE, PROTECTED, and UNPROTECTED can be reported back.
The Security State Context
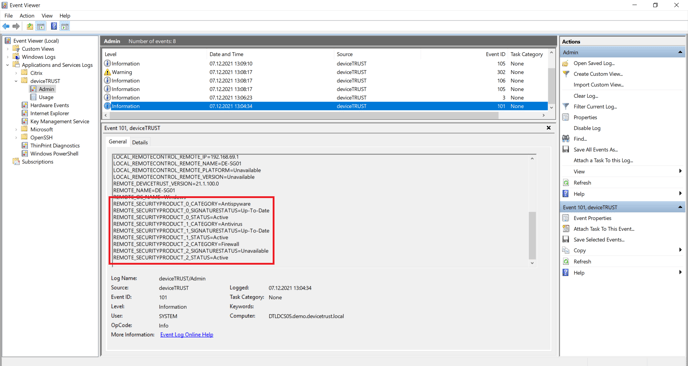
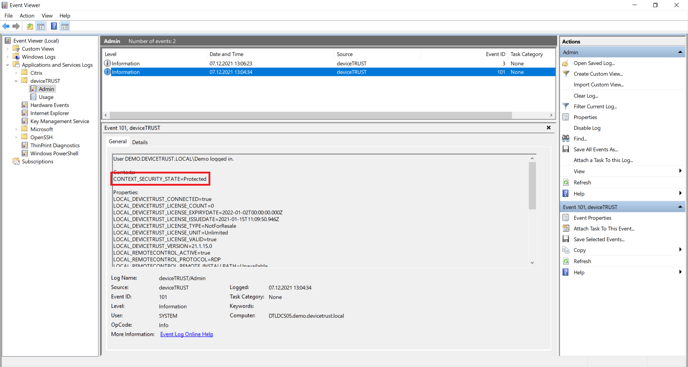
The context value evaluated for a user session can be seen by opening the Windows Event Log on the host system and navigating to APPLICATION AND SERVICE LOGS\DEVICETRUST\ADMIN. Event ID 101 is raised during logon and details the properties and context of the users’ virtual session.
Virtual session properties and contexts
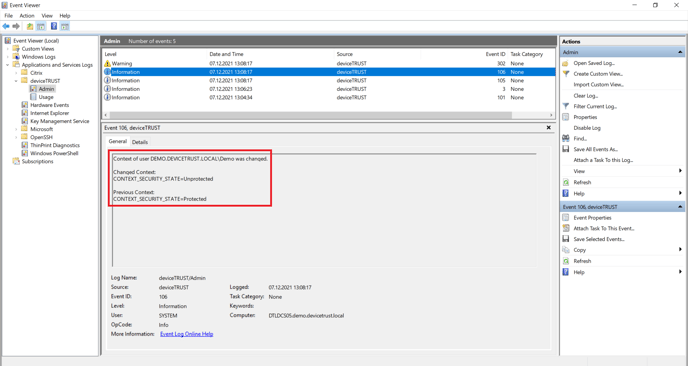
In the above example, we can force a context change on the remote device by, for example, disabling Microsoft Defender Firewall and looking at how the corresponding context updates. To check this, open the Windows Event Log on the host system, navigate to APPLICATION AND SERVICE LOGS\DEVICETRUST\ADMIN, and check for Event ID 106, which is raised whenever a context changes value within the users’ session.
Context change audit event
If the context takes the correct value, the logic for the context definition is correct. If not, the individual properties used within the context definition should also be checked. Check within your context definition which properties are used for the logic and check the accuracy of the logic based on the submitted properties and adjust them if necessary. To do this, open the Windows Event Log on the host system, navigate to APPLICATION AND SERVICE LOGS\DEVICETRUST\ADMIN, and check for Event ID 101, which details the properties and context of the users’ virtual session.
Session properties and contexts